SQLMap: An Open-Source Tool For Uncovering Database Vulnerabilities
SQLMap: An Open-Source Tool for Uncovering Database Vulnerabilities
Related Articles: SQLMap: An Open-Source Tool for Uncovering Database Vulnerabilities
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to SQLMap: An Open-Source Tool for Uncovering Database Vulnerabilities. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
SQLMap: An Open-Source Tool for Uncovering Database Vulnerabilities

The realm of cybersecurity is constantly evolving, with new threats emerging and attackers seeking innovative ways to exploit vulnerabilities. One critical aspect of cybersecurity involves understanding and mitigating database vulnerabilities, which can expose sensitive data and disrupt critical operations. In this context, SQLMap emerges as a powerful and widely recognized tool for security professionals and ethical hackers.
Understanding SQLMap
SQLMap is an open-source penetration testing tool designed to automatically detect and exploit SQL injection flaws in web applications. It operates by sending specially crafted SQL queries to a web server, analyzing the responses to identify potential vulnerabilities. SQL injection attacks exploit weaknesses in the way web applications handle user input, allowing attackers to manipulate database queries and potentially gain unauthorized access to sensitive information.
Key Features of SQLMap
SQLMap’s effectiveness stems from its comprehensive feature set, making it a versatile tool for various security assessments:
- Automated Detection: SQLMap automatically identifies potential SQL injection vulnerabilities, reducing the manual effort required for penetration testing.
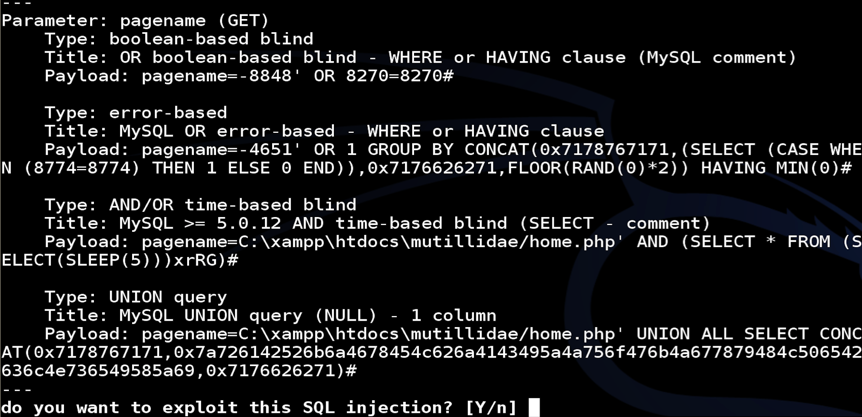
- Multiple Techniques: It utilizes a range of techniques to exploit SQL injection vulnerabilities, including error-based, Boolean-based, time-based, and union-based methods.
- Database Fingerprinting: SQLMap can identify the underlying database management system (DBMS) used by the target application, providing valuable information for tailoring attack strategies.
- Data Extraction: Once a vulnerability is identified, SQLMap can extract data from the database, including sensitive information like user credentials, financial records, and proprietary data.
- Payload Generation: The tool generates custom payloads for exploiting vulnerabilities, enabling targeted attacks based on the identified DBMS and vulnerability type.
- Command Execution: SQLMap allows for remote command execution on the database server, potentially granting attackers complete control over the system.
- Tamper Scripts: These scripts manipulate SQL queries to bypass security measures and evade detection by web application firewalls (WAFs).
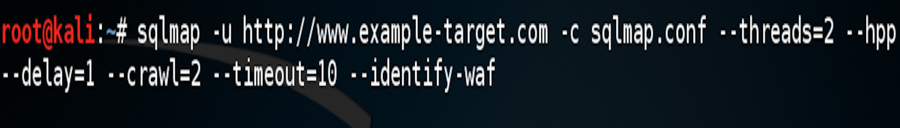
- Extensive Options: SQLMap provides numerous command-line options for customizing its behavior, allowing users to tailor the tool to specific testing requirements.
The Importance of SQLMap in Cybersecurity
SQLMap plays a crucial role in cybersecurity by:
- Identifying and Exploiting Vulnerabilities: It helps security professionals proactively identify and exploit SQL injection vulnerabilities, enabling them to patch security holes and prevent potential attacks.
- Enhancing Security Awareness: By demonstrating the potential impact of SQL injection attacks, SQLMap raises awareness among developers and security professionals about the importance of secure coding practices and database hardening.
- Facilitating Penetration Testing: It empowers ethical hackers and security researchers to conduct comprehensive penetration tests, simulating real-world attack scenarios and identifying vulnerabilities that could be exploited by malicious actors.
- Improving Security Posture: By identifying and mitigating SQL injection vulnerabilities, organizations can strengthen their security posture, reducing the risk of data breaches and financial losses.
Using SQLMap Responsibly
While SQLMap is a powerful tool for ethical hacking and security assessments, it is essential to use it responsibly. Abusing this tool for malicious purposes is illegal and unethical. The following guidelines promote responsible use:
- Obtain Proper Authorization: Always obtain explicit permission from the target organization before conducting any security assessments.
- Respect Privacy and Confidentiality: Do not exploit vulnerabilities to access or disclose sensitive information without authorization.
- Follow Ethical Hacking Principles: Adhere to ethical hacking principles, such as the "Do No Harm" principle, and avoid causing any unnecessary damage or disruption.
- Report Vulnerabilities: If you discover vulnerabilities, report them to the responsible parties for remediation.
FAQs About SQLMap
Q: Is SQLMap legal to use?
A: SQLMap itself is a legal tool for security research and penetration testing. However, using it without proper authorization or for malicious purposes is illegal and unethical.
Q: How can I learn to use SQLMap?
A: Numerous online resources, including tutorials, documentation, and online courses, provide comprehensive guidance on using SQLMap effectively.
Q: What are the risks associated with using SQLMap?
A: Using SQLMap incorrectly or without proper authorization can lead to legal consequences, damage to the target system, and potential data breaches.
Q: How can I protect my web application from SQL injection attacks?
A: Implementing secure coding practices, using parameterized queries, and implementing input validation are essential steps to mitigate SQL injection vulnerabilities.
Tips for Using SQLMap Effectively
- Thorough Research: Before using SQLMap, conduct thorough research on the target application to understand its architecture, vulnerabilities, and potential attack vectors.
- Start with Basic Techniques: Begin with basic SQL injection techniques and gradually move towards more complex methods as you gain experience.
- Test Thoroughly: Test different input fields, parameters, and attack vectors to ensure comprehensive coverage.
- Document Findings: Document your findings, including the identified vulnerabilities, exploitation techniques, and remediation recommendations.
- Stay Updated: Keep your SQLMap installation updated to benefit from new features and security improvements.
Conclusion
SQLMap is a valuable tool for security professionals and ethical hackers, empowering them to identify and exploit SQL injection vulnerabilities. By understanding the capabilities and responsible use of this tool, organizations can enhance their security posture, mitigate risks, and protect sensitive data. Remember that using SQLMap requires ethical considerations and proper authorization. By adhering to responsible practices and leveraging its potential for good, SQLMap can contribute significantly to a more secure digital landscape.





Closure
Thus, we hope this article has provided valuable insights into SQLMap: An Open-Source Tool for Uncovering Database Vulnerabilities. We hope you find this article informative and beneficial. See you in our next article!