Unveiling The Power Of Attack Maps: A Comprehensive Guide To Cybersecurity Strategy
Unveiling the Power of Attack Maps: A Comprehensive Guide to Cybersecurity Strategy
Related Articles: Unveiling the Power of Attack Maps: A Comprehensive Guide to Cybersecurity Strategy
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Unveiling the Power of Attack Maps: A Comprehensive Guide to Cybersecurity Strategy. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Unveiling the Power of Attack Maps: A Comprehensive Guide to Cybersecurity Strategy

In the ever-evolving landscape of cybersecurity, organizations face an intricate web of threats. Navigating this complex terrain demands a proactive approach, one that goes beyond reactive measures and embraces a strategic understanding of potential vulnerabilities. This is where the concept of an attack map emerges as a powerful tool, offering a comprehensive framework for analyzing and mitigating cyber risks.
Understanding the Essence of Attack Maps
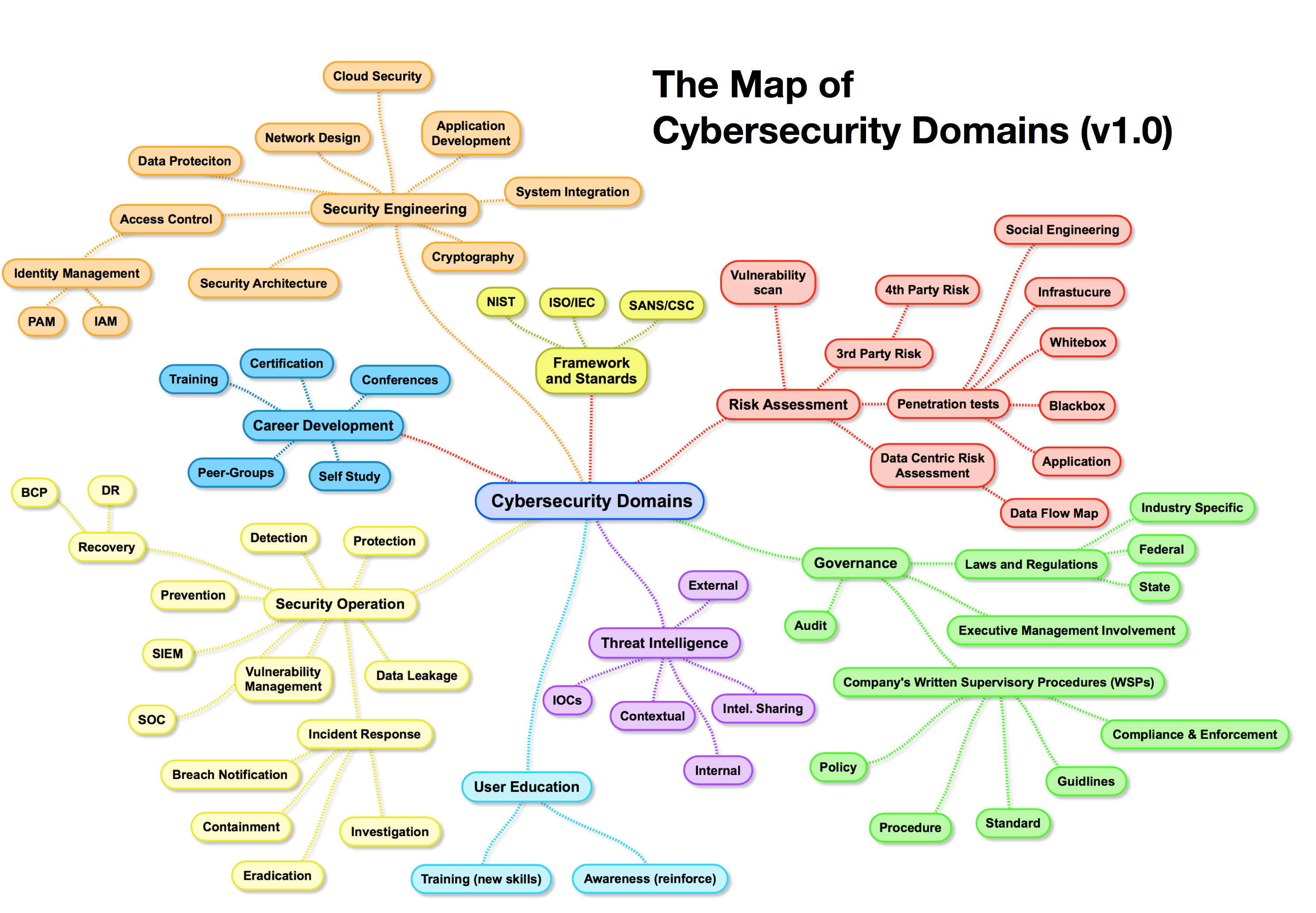
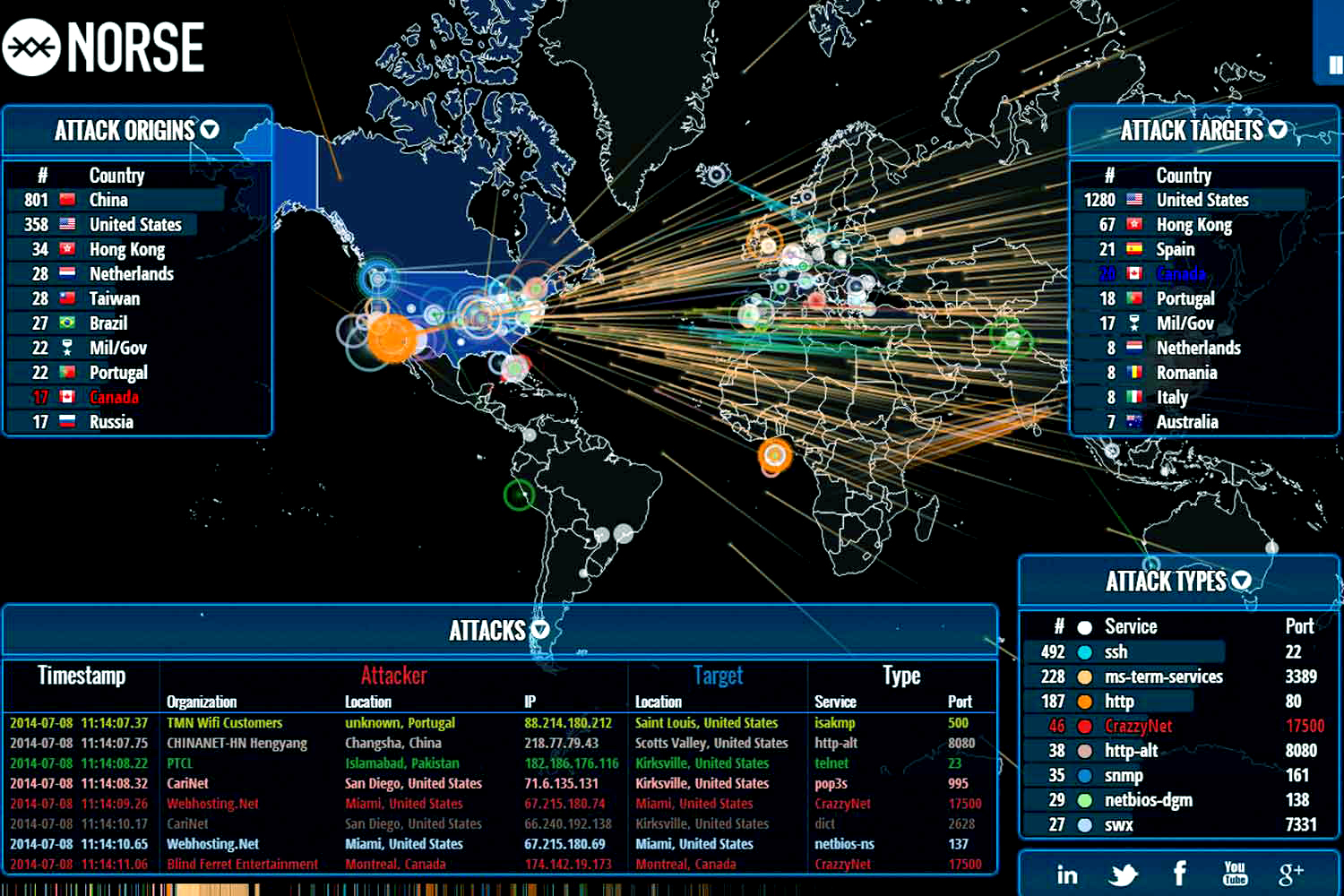
An attack map, often referred to as a threat map or cyber attack map, serves as a visual representation of an organization’s digital landscape, highlighting potential attack vectors and the associated vulnerabilities. It essentially acts as a roadmap for cyber attackers, providing a detailed blueprint of how they might exploit weaknesses to compromise systems and steal sensitive data.
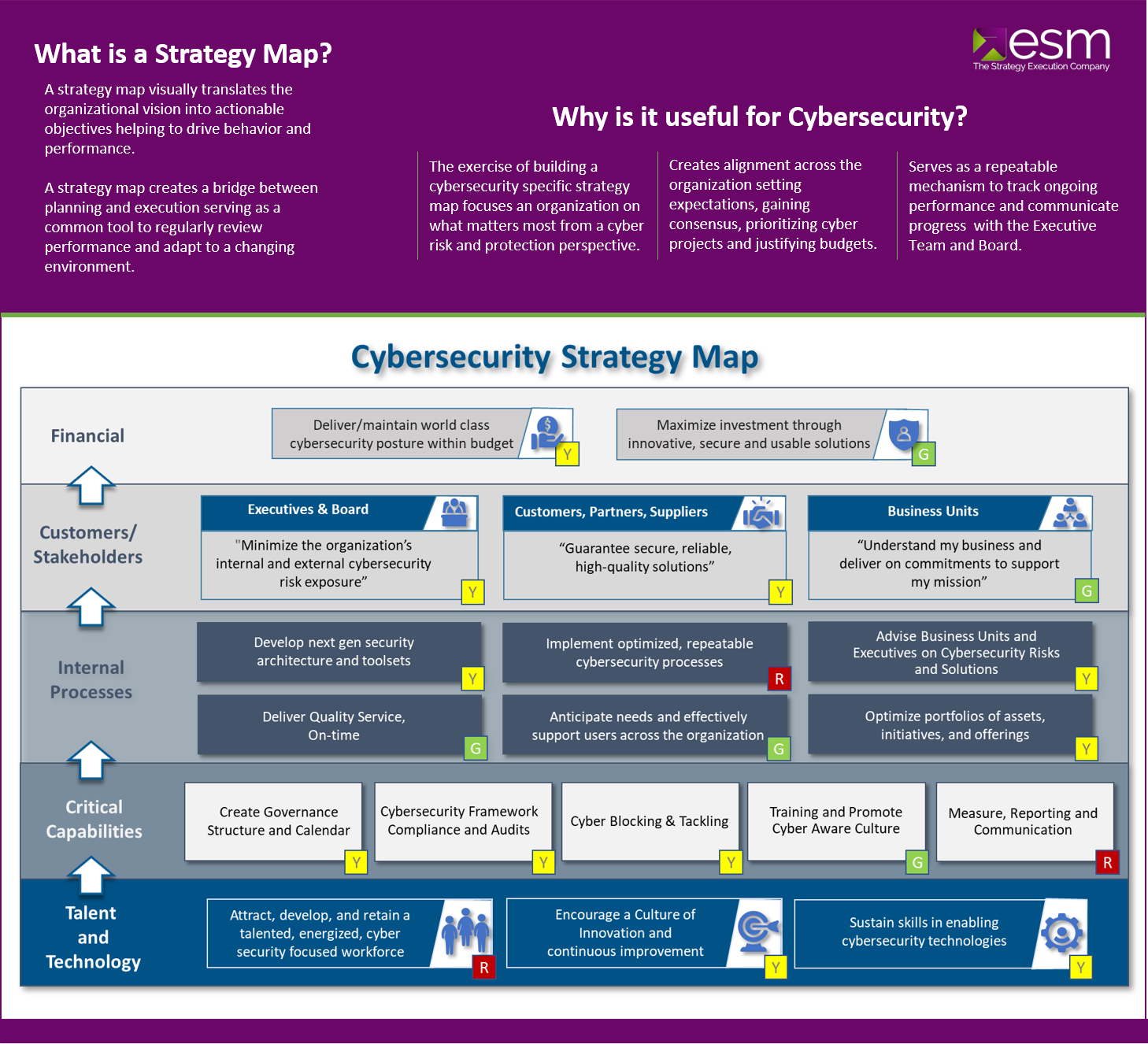
Benefits of Implementing Attack Maps
The strategic value of attack maps lies in their ability to:
1. Proactive Risk Assessment: By visualizing potential attack paths, attack maps enable organizations to proactively identify and assess vulnerabilities, allowing them to prioritize mitigation efforts and allocate resources effectively.
2. Enhanced Threat Intelligence: Attack maps foster a deeper understanding of the threat landscape, providing insights into the tactics, techniques, and procedures (TTPs) employed by adversaries. This intelligence empowers organizations to anticipate and counter evolving threats.
3. Improved Security Posture: By identifying critical assets and vulnerabilities, attack maps facilitate the development of robust security controls, including firewalls, intrusion detection systems (IDS), and multi-factor authentication.
4. Optimized Incident Response: Attack maps provide a clear roadmap for incident response teams, enabling them to quickly identify the affected systems, isolate the breach, and implement containment measures.
5. Improved Communication and Collaboration: Attack maps serve as a common language for security teams, fostering effective communication and collaboration between different departments, including IT, security, and business stakeholders.
Building a Robust Attack Map
Crafting an effective attack map requires a systematic approach:
1. Define the Scope: The initial step involves clearly defining the scope of the attack map, identifying the critical assets and systems to be included.
2. Identify Attack Vectors: This involves brainstorming potential attack paths, considering various techniques such as phishing, malware, social engineering, and brute force attacks.
3. Analyze Vulnerabilities: Each identified attack vector should be analyzed to determine the associated vulnerabilities, such as weak passwords, outdated software, or misconfigured security settings.
4. Prioritize Risks: Based on the severity and likelihood of each attack vector, vulnerabilities should be prioritized, focusing on the most critical threats first.
5. Implement Mitigations: Once vulnerabilities are identified, appropriate security controls should be implemented to mitigate the risks, including patching software, strengthening access controls, and implementing security awareness training.
6. Continuously Monitor and Update: The attack map is a living document that requires regular monitoring and updates to reflect changes in the threat landscape, organizational assets, and security controls.
FAQs About Attack Maps
Q: Who should be involved in creating an attack map?
A: Creating an effective attack map requires a collaborative effort involving various stakeholders, including security professionals, IT specialists, business leaders, and potentially external security consultants.
Q: What are some common attack vectors to consider in an attack map?
A: Common attack vectors include phishing, malware, social engineering, brute force attacks, SQL injection, cross-site scripting (XSS), and denial-of-service (DoS) attacks.
Q: How often should an attack map be reviewed and updated?
A: The frequency of review and updates depends on the organization’s risk profile and the dynamic nature of the threat landscape. Ideally, attack maps should be reviewed and updated at least annually, or more frequently if significant changes occur in the organization’s security posture or the threat environment.
Q: What are some tools that can be used to create an attack map?
A: Several tools are available to assist in creating attack maps, including:
- Threat modeling tools: These tools provide structured frameworks for analyzing threats and vulnerabilities.
- Security information and event management (SIEM) systems: SIEM tools can be used to collect and analyze security data, providing insights into potential attack vectors.
- Vulnerability scanners: These tools identify and assess vulnerabilities in systems and applications.
- Diagraming tools: Tools like Visio or Lucidchart can be used to visually represent the attack map.
Tips for Effective Attack Map Implementation
1. Start Small: Begin by creating an attack map for a specific system or application, gradually expanding the scope as you gain experience.
2. Focus on Critical Assets: Prioritize the most critical assets and systems, those that are essential for the organization’s operations and contain sensitive data.
3. Use Clear and Concise Language: The attack map should be easily understandable to all stakeholders, using clear and concise language.
4. Regularly Review and Update: Attack maps are living documents that require regular review and updates to reflect changes in the threat landscape, organizational assets, and security controls.
5. Collaborate with Stakeholders: Involve key stakeholders from different departments to ensure that the attack map reflects the organization’s specific needs and priorities.
Conclusion
In the ever-evolving landscape of cybersecurity, proactive risk management is paramount. Attack maps provide a powerful tool for organizations to visualize and analyze potential threats, identify vulnerabilities, and develop effective security strategies. By embracing the principles of attack mapping, organizations can strengthen their security posture, mitigate risks, and build resilience against cyber threats.



Closure
Thus, we hope this article has provided valuable insights into Unveiling the Power of Attack Maps: A Comprehensive Guide to Cybersecurity Strategy. We hope you find this article informative and beneficial. See you in our next article!